
Playbooks bring Security Orchestration Automation and Response (SOAR) capabilities to the C3M Cloud Control Platform. It helps streamline the security operations via a flexible, customizable, and extensible framework that can support multiple remediations or actions for cloud entities.
The Playbooks capability is
available for AWS, GCP and Azure

The Playbook Framework
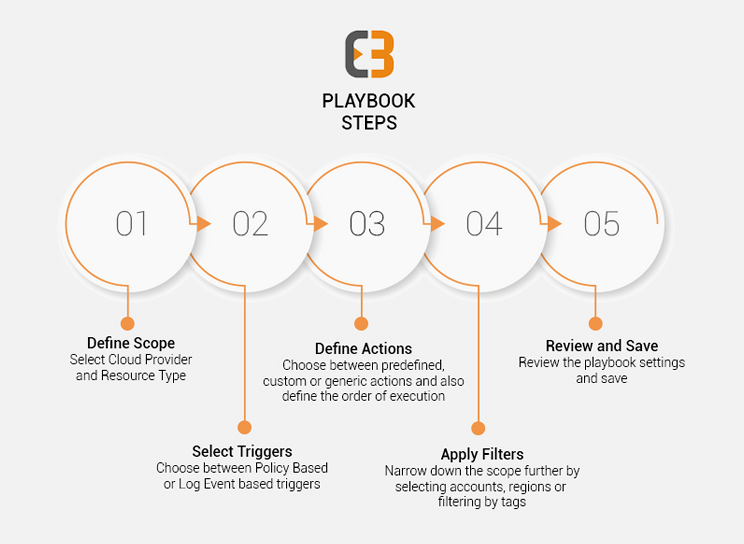
Now, let’s look at some actions that come bundled with Playbooks:
Perform actions on cloud resources
Remove Public Access to a EC2
Encrypt a S3 Bucket
Add tags to supported resource types etc.
Notifications on policy violations
Creating incident tickets
Push violations to SIEM tools
A real-life example
Let’s look into a day in the life of Joe who is a Data Security Analyst at XYZ Company. Joe and his team are responsible for managing and monitoring the data security posture across AWS, GCP and Azure infrastructures (3 clouds that XYZ Company uses)
Below are the steps that Joe and team follows when they get an alert for Storage Buckets in AWS
- Receive an alert that a S3 bucket is exposed to the public internet.
- Look up the S3 Bucket configurations and do a root cause analysis.
- Manually resolve the violation by following a set of instructions.
- Log and record this change in some ticketing system, so that it can be tracked and reported.
- Notify a set of administrators or project owners about the violation and the remediation that was applied.
NOW REPEAT SIMILAR STEPS FOR ALL RESOURCES THAT COME TO HIS QUEUE
Net effect
Joe is flooded with requests, and since the changes are manual the probability of another misconfiguration creeping in cannot be ruled out and as we are all humans – Joe ends up missing one or the other step….
NOT A HAPPY PICTURE
Now let’s look at the same set of events, but this time –
with the help of playbooks in C3M Cloud Control.
THE NEW PROCESS WILL LOOK LIKE THIS
Joe defines a S3 Bucket Playbook and selects cloud security policies that can trigger the playbook. Example – S3 bucket exposed to the public internet
As part of the playbook definition, Joe defines 3 automated actions.
- Remediate the S3 public exposure (happens via an API call)
- Send an email to the Data Security Admins
Joe saves the playbook definition. That’s literally it.
From now on, all detected S3 Bucket violations will automatically trigger Joe’s playbook which in turn will ensure the following
The S3 Bucket violation is remediated (automatically)
A ServiceNow ticket is created to track the same
Data Security Admins are notified via email.
NET RESULT.
Joe is happy and XYZ Company has a robust response mechanism for data misconfiguration threats
Joe is happy and XYZ Company has a robust response mechanism for data misconfiguration threats
Extensible Framework
Customers can also choose to extend the playbook functionalities by writing their own custom actions. Custom Actions can be written using the serverless framework (AWS Lambda, GCP Functions and Azure Functions).
Customers can choose to write these actions in their preferred programming language (Java, NodeJs, Python etc)






