Cloud Infrastructure
Entitlement Management (CIEM)
By 2023, 75% of security failures in the cloud will be a result of inadequate management of identities, access and privileges
What is CIEM?
CIEM Solutions focuses on IAM Governance, mainly by reducing the risk of over-privileged identities in a dynamic multi-cloud infrastructure. CIEM mitigates the risks associated with privilege escalation, compromised credentials and other suspicious access activities by providing deep visibility into cloud entitlements and access risks.
- Monitor & Govern Privileged Users
- Report & Remove Unused Entitlements
- Prevent Insider Threat Attacks
- Auditing and Forensics Capabilities
- Identity Risk Score
- Anomaly Detection and Alerting
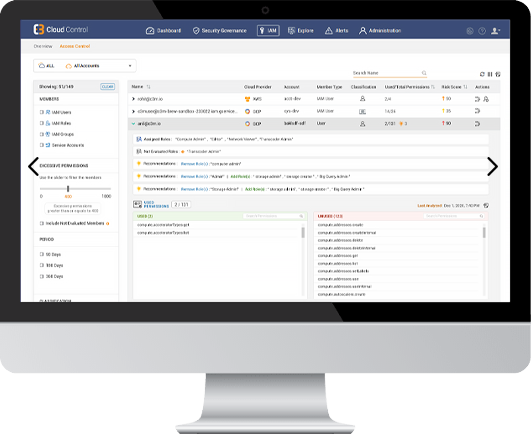
C3M Cloud Access Control helps ascertain:
C3M Core CIEM Capabilities
Visibility and Inventory
- Inventory of all Human and Machine Identities across Multi Cloud
- View Overall IAM Compliance Score by Cloud Account or Account Groups
- Detect identities and resources with excessive permissions and entitlements
- View and monitor Access Key usage
- Deep visibility into entitlements and access patterns
Auditing
- Timeline view of changes to sensitive resources
- Track recent access changes across cloud infrastructure
- Track user activities generate audit reports
- View traffic patterns in the network
- Audit granular permissions of IAM users, roles and service accounts
Governance
- Enforce predefined and custom IAM policies
- One Click Remediation for unused entitlements
- Rightsize roles across cloud service providers
- Diagnose and fix IAM failures
Reporting
- Generate IAM Compliance reports
- Generate IAM Executive Summary reports
- Generate Activity Audit Report for Human and Machine users
- Generate User Entitlements reports
Resources

Protecting Cloud Infrastructure from Ransomware Threats
Eureka, Eureka! That’s How to Protect Cloud Infrastructure from Ransomware Like Archimedes, we can’t wait to tell people of our discovery. Enterprises around the world

C3M Playbooks
Playbooks bring Security Orchestration Automation and Response (SOAR) capabilities to the C3M Cloud Control Platform. It helps streamline the security operations via a flexible, customizable,

Are your IAM Access Keys Safe?
The Breach The last few months have seen multiple data breaches across organisations in the retail, stock brokerage, restaurant chain, FinTech space etc in India.

